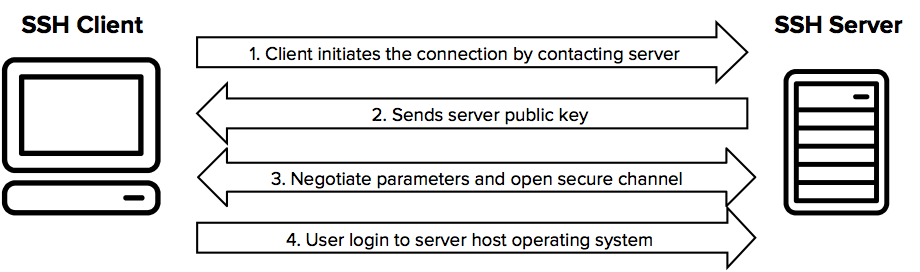
What is a Secure Shell (SSH)?
It’s a network protocol that allows two computers connected by an electrical channel to communicate with one another. Secure Shell ensures data security. It was developed in the aftermath of the sniffing attack at Helsinki University of Technology. Previously, the Telnet protocol was quite popular at the time of the sniffer assault, but today the secure shell protocol has surpassed it and is widely used.
Advantage of SSH:
SSH protects data by encrypting it before sending it and then decrypting it at the designated place. SSH allows the user to issue a command that is understood and performed by the listening server on the remote computer. It’s also utilized for service monitoring and routing, and it’s used in running applications or even for file transfers. SSH gives the user more control over their site and gives them more freedom in managing it.
SSH Attack:
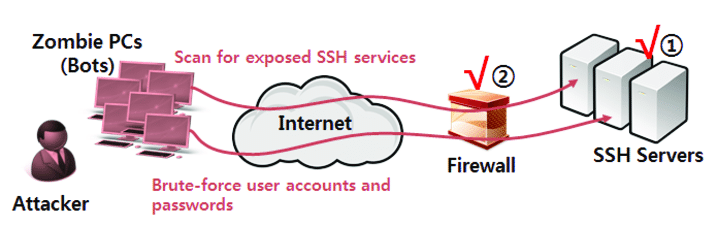
Even though SSH is more secure, hackers will have their own way to make it insecure. One of the famous attacks is SSH brute-force.
- Attackers try a variety of login and password combinations until they find the appropriate one and get access to an account or a server.
- The most serious flaw with a brute-force attack is that many systems are set up to block attackers after a certain number of failed login attempts.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
- The process is reversed in an SSH brute-force attack. Rather than attempting thousands of username and password combinations on a single server, the offenders attempt one username and password combination on thousands of servers.
- Employees choose a weak password, which makes the attack possible, and hackers don’t have to worry about lockout mechanisms because each server only records one failed login attempt at most.
- It’s also known as a spray-and-pray attack, which means the criminals are betting that if they hit many servers, one of them would let them in. It might be effective, but as you can see, it’s not very useful if the criminals have their current focus on a certain target.
Best Security Practices for Mitigating SSH-based Attacks:
However, SSH is far more secure than FTP, if you don’t follow the best practices for hardening it effectively, it can still be exploited and hacked. Here we have a few security practices to harden ssh:
1-Disable Root Login
- SSH servers, in addition to having the port set to 22 by default, allow root login on most Linux and Unix operating systems.
- Anyone can connect to port 22, use the root user as the default, and then conduct a slew of brute force attempts against your public server’s IP address.
Also Read: Threat Hunting Using Powershell and Fileless Malware Attacks
- If you have password authentication enabled on your SSH service and your root password is weak, you are very likely to be hacked. As a consequence, disabling root login is one of the oldest and most widely used methods for preventing system compromise on new OS installations.
- You can evaluate this by letting the SSH installation alone, parsing the /var/log/secure file, and counting the number of brute force attacks you receive in a few hours.
- Even if you use strong passwords, it’s always a good idea to disable root login and instead use a primary SSH user, so that if you need root access, you can use the su command.
2-Empty Passwords Must Be Disabled
On Linux and Unix, administrators can create users with blank passwords. And if you want to keep attackers out of your SSH servers, this can be a disadvantage. As a consequence, the best thing you can do is block remote logins for accounts with an empty password by modifying the sshd_config file, which is simple to perform.
Query:
nano -w /etc/ssh/sshd_config ; Then set: PermitEmptyPasswords no
3-Set a custom SSH port
Since SSH is configured to listen on port 22, which is well-known among attackers and security tools/port scanners that conduct brute force attempts. While obscurity considers this to be security, it does help eliminate a lot of noise on port 22. Edit the SSH main config file and change the port from 22 to different ports like 899.
Also Read: Threat Hunting with Windows Event IDs 4625 & 4624
4-Configure a custom SSH warning banner
Setting a custom welcome banner for SSH connections is a good practice for all Linux and Unix machines. This isn’t so much a security tip as it is a security warning for any unauthorized access to your systems. A warning banner will appear once the user has acquired access.
5-On laptops and desktops, disable the OpenSSH server
However many Linux distributions come with OpenSSH Server enabled by default (which implies root login is enabled, the service listens on port 22, and so on), and SSH access is required to work remotely on dedicated, VPS, and cloud servers. It is not required on personal computers. To avoid unwanted attacks, make sure to remove the OpenSSH server.
6-SSH Passwordless login
In this scenario, the ideal option is to replace outdated password-based logins with key-based logins, which will improve your security while also allowing you to set a quick fast SSHlogin without any prompts, as is the case when the SSH password is required. Password-based logins are good if you have a strong collection of characters, such as symbols, uppercase, lowercase, and digits, but they all risk being brute-force cracked at some point. You can also execute automated processes that require SSH connections using SSH key-based logins.
Also Read: Splunk Architecture: Forwarder, Indexer, And Search Head
7-Limit the number of times an attacker can try to log in with a failed password
Setting a modest limit for the number of times an attacker may try to log in with a failed password is another smart technique to defend against brute force attacks. The MaxAuthTries setting might assist you in preventing such attacks.
Query:
nano -w /etc/ssh/sshd_config ; Search for MaxAuthTries. Set it to 3, as MaxAuthTries 3
8-Use TCP Wrappers
TCP Wrappers works using two files: /etc/hosts.allow and /etc/hosts.deny.
Examples:
- Use the following query to block all connections from an unknown host:
- nano -w /etc/hosts.deny
- ALL : ALL
- You can add the following code to the allow file if you wish to enable access from your static home IP, for example:
- nano -w /etc/hosts.allow
- sshd : 1.0.0.1
- You can use either your real public IP or your private LAN IP to replace the IP. This will allow you to block all the others while allowing only the IP addresses you specify.
9-For ssh users and keys, use strong passwords/passphrases
If you can’t set an ssh-key and must rely on login passwords, or if you want to use a passphrase for your keys, make sure to use a strong character combination. Following these guidelines will assist you in creating a strong password/password and avoiding being hacked during a brute-force attack.
- If feasible, include uppercase and lowercase letters, symbols, numbers, and up to 8 characters.
- Avoid using: Dictionary-based words, Personal birthday and anniversary dates, Family and pet names.
10-Enable login notifications over email/alert
Setting up a short script to generate an alert whenever someone logs in as root over SSH is one of the finest things you can do to keep a watch on your incoming SSH connections.
11-Filter the SSH port on the firewall:
One of the first things that all servers should do after the OS is installed is set up a server-side software firewall. ConfigServer Security & Firewall (CSF) from ConfigServer is one of the most popular and effective firewalls we’ve encountered. CSF is simple to install on plan-based distros (without a control panel), and filtering the ports is even simpler.
12-Automatically identify and block SSH brute force attacks
It is simple to detect and block SSH brute force attacks. The manual method entails parsing system logs to determine who is attempting to connect to the server and then blocking them with the system firewall. There are, however, a number of solutions that can automate and reduce those tedious tasks for you. SSHGuard, Fail2ban, and DenyHosts are just a few of the technologies available to protect against brute force attacks.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
13-SSH should be kept up to date
The most important guideline to remember is to maintain your server packages up to date, which includes OpenSSH. This should be sufficient to keep your OpenSSH server safe from emerging vulnerabilities.
14-Set the Idle Timeout Interval
Setting the idle timeout interval allows you to terminate SSH sessions that aren’t in use. For example, if we set 240, which equals 4 minutes, the SSH session will be automatically logged out once the timeout has been reached.
Conclusion:
As previously stated, SSH offers numerous advantages, but it must be maintained with appropriate security measures. On your Unix/Linux operating system, the preceding SSH security guidelines will assist you to prevent the majority of the common SSH attacks.